Extreme VoIP Troubleshooting – Decrypt TLS SIP and SRTP
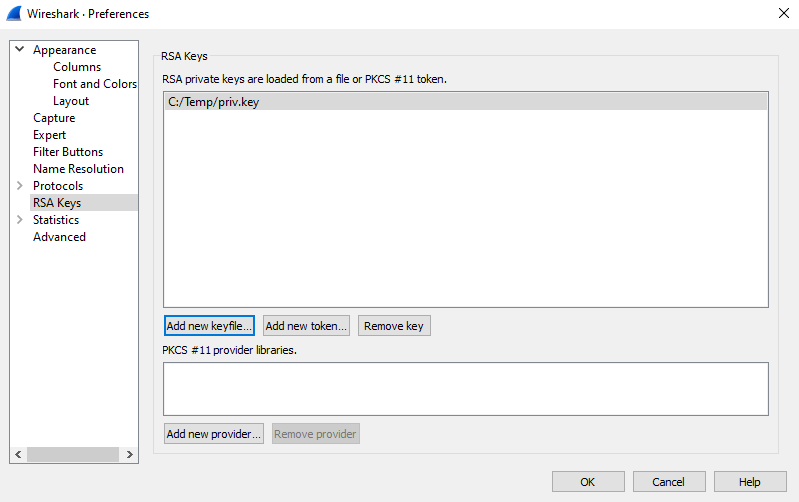
1) Ensure Wireshark has the private key for the “server” side of the TLS conversation.
This is under Edit>Preferences>RSA Keys and the private key should be PEM formatted with an extension of .pem or .key
After you have the key file loaded, open the PCAP you are working with.
IMPORTANT: Your packet capture must contain the TLS negotiation for the port numbers in question that shows “Client Hello”, “Server Hello”, etc. Without this information Wireshark cannot decode any subsequent TLS packets. Therefore, you should probably have a capture that begins 15 minutes before the call you’re looking at.
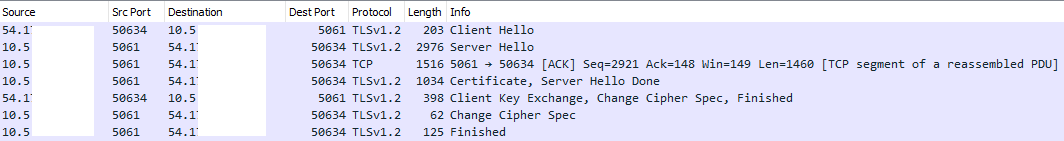
2) Once your TLS SIP packets are decrypted, go to the INVITE for the call you’d like to decrypt.
NOTE: If Wireshark displays “Linux Cooked Capture” or SLL on the line underneath “Frame” (instead of Ethernet II) then you’ll need to do some additional work to decrypt the packets. Linux Cooked Capture usually means the PCAP is for multiple interfaces and srtp-decrypt will not be able to decode them as-is. Tracewrangler may be able to help you.
The SDP will contain the inline key we need. In this case the key is 2U9eiAwx0eg0jkjf0X1idOmqBlO7H9lokrrUsnEO.
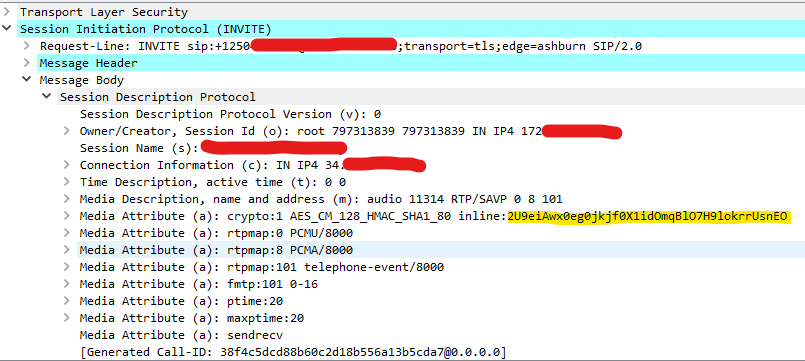
At this point we have the info we need to decrypt the audio from the INVITE side of the call. If you need to decrypt audio in the other direction simply grab the inline key from the SDP of the OK packet instead of the INVITE packet.
3) The next step is to filter the audio packet from the INVITE side of the call. In Wireshark you can do this with a filter like:
udp.port == 11314 and ip.src == 34.0.0.1
4) Now save using File>Export Specified Packets and check that only “Displayed” packets will be saved.
Save as a .pcap type file and transfer it over to a linux PC.
5) On the linux machine go to /usr/src and run the following commands:
git clone https://github.com/gteissier/srtp-decrypt.git
cd srtp-decrypt/
make
cd srtp-decrypt
./srtp-decrypt -k 2U9eiAwx0eg0jkjf0X1idOmqBlO7H9lokrrUsnEO < /path/to/audio-srtp.pcap > /path/to/audio-decrypted.txt
Obviously you want to replace the text after –k with the inline key we retrieved from the SIP packet, and modify the paths to the input and output files as needed.
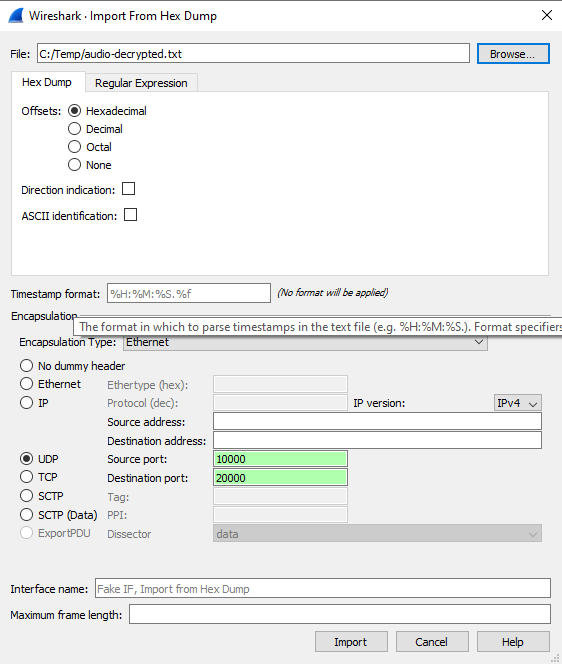
6) Transfer the .txt output file back to your Windows PC and import it to Wireshark using File>Import HEX Dump
Choose UDP as the protocol and input some fake port numbers.
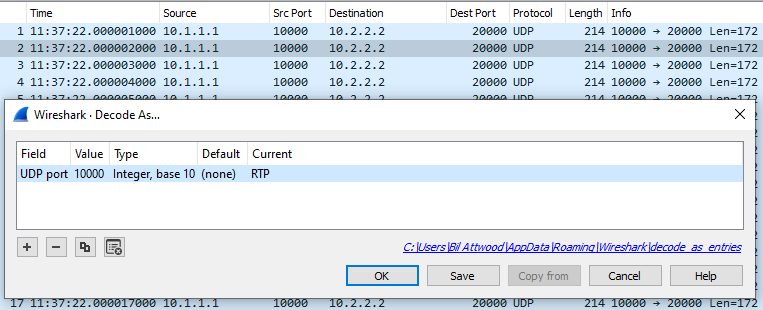
7) Next, right click on one of the lines and choose “Decode As”, then pick RTP for the “Current” column.
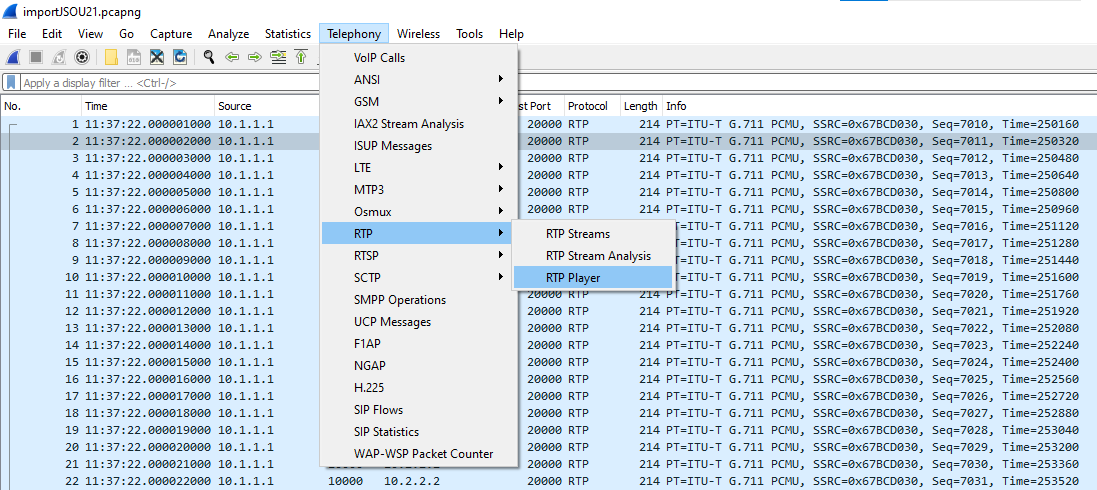
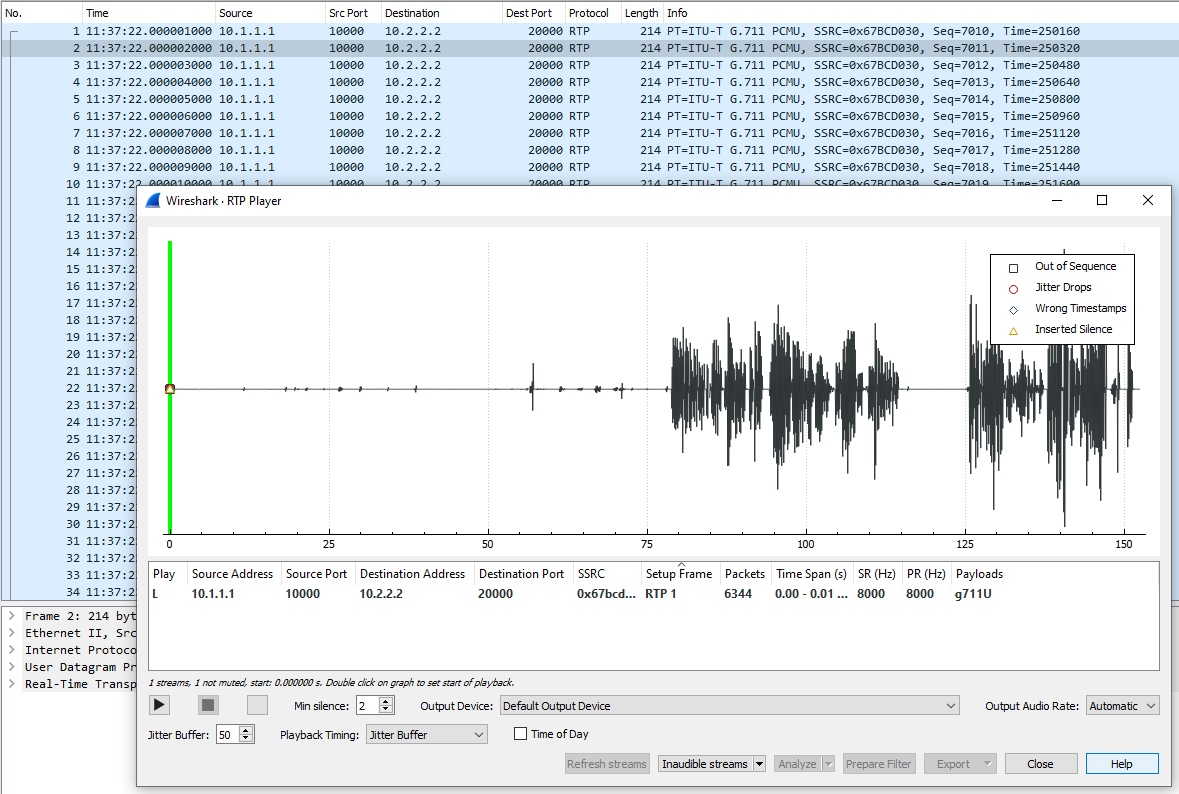
8) Finally, you can go to Telephony>RTP>RTP Player and the audio will be available!
Atcom Professional VoIP Troubleshooting
Contact Atcom today if you are interested in our professional VoIP troubleshooting services!
VoIP Troubleshooting Sources:
https://www.acritelli.com/blog/hacking-voip-decrypting-sdes-protected-srtp-phone-calls/
https://github.com/gteissier/srtp-decrypt

